| 1 Apr 2021 |
 sarahjamielewis sarahjamielewis | Happy April Everyone! https://www.wired.co.uk/article/uk-encryption-facebook-home-office-nspcc 🙃 | 16:16:15 |
 @itsagoose:matrix.org @itsagoose:matrix.org | Grr | 20:27:25 |
 @itsagoose:matrix.org @itsagoose:matrix.org | I personally don't use Facebook products but I'm glad they're moving to use E2EE | 20:27:51 |
 @beardog:amorgan.xyz @beardog:amorgan.xyz | It's always in the name of protecting children. | 23:16:06 |
 @beardog:amorgan.xyz @beardog:amorgan.xyz | I created a reddit throw away over Tor and i think it was instantly shadow banned. I try to visit my profile without being logged in and it says no user exists, and my posts don't show up to non logged in users either. It doesn't appear to be a subreddit specific thing
Also every time i log out reddit my password becomes invalid and to login i have to reset
Between this and reddit flat out preventing Tor from even loading it's main site interface, reddit is highly anti-privacy (they also removed fine-grained privacy controls recently and added an opt-out stalker feature to tell when users are online) | 23:22:30 |
| 2 Apr 2021 |
|  mconley changed their display name from mconley to mconley|away. mconley changed their display name from mconley to mconley|away. | 16:07:37 |
 sarahjamielewis sarahjamielewis | In reply to @beardog:amorgan.xyz
It's always in the name of protecting children. Reddit has gotten so much worse in recent years. They've never been great with Tor, but jumping through the hoops with email verification used to prevent shadow banning (though anonymous email is itself a hard thing to find these days). | 16:52:46 |
| 3 Apr 2021 |
 @beardog:amorgan.xyz @beardog:amorgan.xyz | Jeremy hammond is out of prison, and he had to install state mandated spyware as part of his release. How did we get to this point where this is acceptable... | 20:33:34 |
 @beardog:amorgan.xyz @beardog:amorgan.xyz | Out of pure chance I got a tor circuit with an exit node that uses the same IP as one of the servers of my VPN provider... Probably not great | 23:43:58 |
| 4 Apr 2021 |
 @ykf5jjhhub8f:matrix.org @ykf5jjhhub8f:matrix.org | Yes, if you use vpn you should try to exclude them. First and last are important. | 03:40:02 |
| 5 Apr 2021 |
|  mconley changed their display name from mconley|away to mconley. mconley changed their display name from mconley|away to mconley. | 14:44:52 |
| 6 Apr 2021 |
 sarahjamielewis sarahjamielewis | Reposting this here in case anyone has any relevant thoughts / info : https://twitter.com/SarahJamieLewis/status/1379230409897111553 | 22:25:30 |
 sarahjamielewis sarahjamielewis | 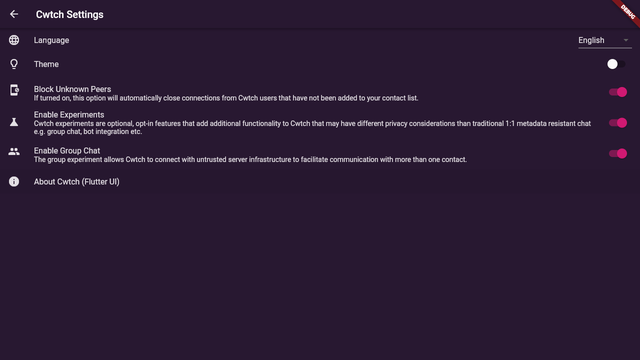
Download Screenshot_20210406_150622.png | 22:27:54 |
 sarahjamielewis sarahjamielewis | Also here is a fund Cwtch WIP screenshot since it has been a while... | 22:28:02 |
| 7 Apr 2021 |
 @ykf5jjhhub8f:matrix.org @ykf5jjhhub8f:matrix.org | About this mobileCoin and sgx do you guys just think the sgx will brack and then the value is 0? Or are there other risks? | 04:00:20 |
 sarahjamielewis sarahjamielewis | My prediction is that sometime in 2022 there will be a new attack impacting SGX and that the paper will draw a direct line between the viability of the attack and a consensus attack on mobilecoin. In response mobilecoin will invoke some fuzzy notions of centralised trust anchors dressed up in the language of the "decentralized quorums" as reasons for why such an attack would fail in practice but ultimately provide vague plans to remove SGX from their system, probably replacing it with some other secure enclave. This cycle will repeat endlessly because there is a subset of people who will always believe secure enclaves are an actual thing that can exist rather than a cute oracle they invoke in paper to make their scheme secure. | 18:57:24 |
 sarahjamielewis sarahjamielewis | * My prediction is that sometime in 2022 there will be a new attack impacting SGX and that the paper will draw a direct line between the viability of the attack and a consensus attack on mobilecoin. In response mobilecoin will invoke some fuzzy notions of centralised trust anchors dressed up in the language of the "decentralized quorums" as reasons for why such an attack would fail in practice but ultimately provide vague plans to remove SGX from their system, probably replacing it with some other secure enclave. This cycle will repeat endlessly because there is a subset of people who will always believe secure enclaves are an actual thing that can exist rather than a cute notion they invoke in their papers to make their scheme secure. | 18:59:26 |
 sarahjamielewis sarahjamielewis | https://eprint.iacr.org/2021/442 | 19:06:53 |
 @hackbunny:matrix.org @hackbunny:matrix.org | In reply to @sarahjamielewis:matrix.org
My prediction is that sometime in 2022 there will be a new attack impacting SGX and that the paper will draw a direct line between the viability of the attack and a consensus attack on mobilecoin. In response mobilecoin will invoke some fuzzy notions of centralised trust anchors dressed up in the language of the "decentralized quorums" as reasons for why such an attack would fail in practice but ultimately provide vague plans to remove SGX from their system, probably replacing it with some other secure enclave. This cycle will repeat endlessly because there is a subset of people who will always believe secure enclaves are an actual thing that can exist rather than a cute notion they invoke in their papers to make their scheme secure. what's your take on the use of SGX in Signal to hide phone numbers from the server? | 22:10:20 |
 @hackbunny:matrix.org @hackbunny:matrix.org | lately I've been wondering if it means that SGX is already compromised by three-letter agencies | 22:10:56 |
 @hackbunny:matrix.org @hackbunny:matrix.org | SGX + phone numbers as mandatory user identifiers despite criticism is a fishy combo | 22:11:39 |
 sarahjamielewis sarahjamielewis | There are a couple of levels worth considering for nuance:
SGX as implemented right now on most systems is fundamentally broken, many times over. There are several CPU bugs where patch rates are questionable and many others that are outright unpatchable (i.e. Load Value Injection). Last I checked Intels official response to this was "as long as you trust the OS to mitigate things properly it's not exploitable in the real world) which might be fine under some threat models, but is definitely not under ones we care about for something like Signal.
So anything that invokes SGX in its threat model is likely broken in practice, if not in theory. Invoking the "well I'm sure Signal patched their server OS" doesn't resolve the brokenness because it forces you to accept a trust assumption. (if you are willing to invoke that trust assumption then you don't need to bother with SGX at all - just trust signal to run the source code they say they run (which they sometimes don't publish for a year...but that's another thing entirely))
But, because the entire point of invoking a secure enclave is to protect your users from yourself then it's not just a case of auditing the source code, but also the entire operating system stack, continually - because the moment you take your eyes away from it it can be swapped out with something that makes it vulnerable.
In any case, as far as government agencies are concerned there is a spectrum from a targeted hack to an explicit backdoor. If a government could force Signals cooperation then there are likely far easier places to put a backdoor (like the client software, via a targeted poisoned appstore "upgrade"), so in terms of realistic exploits on the SGX side I'd be more concerned with a targeted hack (probably from states outside of jurisdictions where Signal operates).
| 22:53:39 |
 sarahjamielewis sarahjamielewis | Or to summarise: under funded grad students have been demonstrating SGX compromises for years, so feel free to extrapolate the capabilities of your favourite well funded state actor from that. | 22:55:41 |
 @beardog:amorgan.xyz @beardog:amorgan.xyz | Sarah have you ever read about the stuff that happened legally with Freenet in recent years? It is interesting outside of the Freenet sphere as it involves american LE allegedly using bad math and also my interpretation of some of the leaked documents was that LE was questioning people for merely using Freenet either because of the bad math or because they just assumed people using the software have to bad (in fairness there is a good bit of terrible on freenet)
The recent/pending legal trials are happening in my state (MO), and i'm friends with someone who is testifying on the math used
Imagine if LE randomly decided that Tor users (or specifically Cwtch traffic pattern) should be questioned/interrogated, that's how this is. | 23:57:13 |
| 8 Apr 2021 |
 joepie91 🏳️🌈 joepie91 🏳️🌈 | In reply to @sarahjamielewis:matrix.org
My prediction is that sometime in 2022 there will be a new attack impacting SGX and that the paper will draw a direct line between the viability of the attack and a consensus attack on mobilecoin. In response mobilecoin will invoke some fuzzy notions of centralised trust anchors dressed up in the language of the "decentralized quorums" as reasons for why such an attack would fail in practice but ultimately provide vague plans to remove SGX from their system, probably replacing it with some other secure enclave. This cycle will repeat endlessly because there is a subset of people who will always believe secure enclaves are an actual thing that can exist rather than a cute notion they invoke in their papers to make their scheme secure. it still kind of amazes me how so many security people who really Should Know Better bought into the idea of SGX as a tamperproof general-purpose secure enclave... often the same people who would have rejected 'secure hardware' years prior | 00:01:51 |
 joepie91 🏳️🌈 joepie91 🏳️🌈 | still not totally sure what magic trick Intel pulled to convince the skeptics | 00:03:18 |
 @hackbunny:matrix.org @hackbunny:matrix.org | In reply to @sarahjamielewis:matrix.org
There are a couple of levels worth considering for nuance:
SGX as implemented right now on most systems is fundamentally broken, many times over. There are several CPU bugs where patch rates are questionable and many others that are outright unpatchable (i.e. Load Value Injection). Last I checked Intels official response to this was "as long as you trust the OS to mitigate things properly it's not exploitable in the real world) which might be fine under some threat models, but is definitely not under ones we care about for something like Signal.
So anything that invokes SGX in its threat model is likely broken in practice, if not in theory. Invoking the "well I'm sure Signal patched their server OS" doesn't resolve the brokenness because it forces you to accept a trust assumption. (if you are willing to invoke that trust assumption then you don't need to bother with SGX at all - just trust signal to run the source code they say they run (which they sometimes don't publish for a year...but that's another thing entirely))
But, because the entire point of invoking a secure enclave is to protect your users from yourself then it's not just a case of auditing the source code, but also the entire operating system stack, continually - because the moment you take your eyes away from it it can be swapped out with something that makes it vulnerable.
In any case, as far as government agencies are concerned there is a spectrum from a targeted hack to an explicit backdoor. If a government could force Signals cooperation then there are likely far easier places to put a backdoor (like the client software, via a targeted poisoned appstore "upgrade"), so in terms of realistic exploits on the SGX side I'd be more concerned with a targeted hack (probably from states outside of jurisdictions where Signal operates).
thank you! I admit my knowledge of SGX is extremely limited, so I wasn't aware that there would be so many ways to get it wrong
speaking of Signal specifically, the threat model I'm thinking of is a pure metadata compromise, where you can reconstruct who's talking with whom, without necessarily knowing what they're saying ("we kill people based on metadata"). besides timing analysis, to me the easiest way seems to be compromising the contact list server: it gives you a "god mode" view over the entire network, it's completely opaque to researchers, you can turn it on and off any time, and Whisper Systems can plausibly deny they knew anything about it. there's a certain degree of secrecy around the Signal servers dictated by anti-censorship considerations that helps here
personally, I'm not too worried about the rogue update attack: it leaves permanent evidence all over the place, it's much harder to plausibly deny, and it would destroy the reputation of Signal and WhisperSystems if it were discovered. easier to compromise the extremely opaque servers (lots of places to hide bad code in a server, too: think SMM, or SGX itself), identify the target through traditional techniques and/or metadata analysis and then phish them with a targeted attack, IMHO. wrt the client I think the most realistic attack is a vulnerability in a third party codec or the VoIP stack, especially on iOS where only iMessage has the privilege to put sensitive code in separate sandboxed processes
| 00:55:30 |
 @hackbunny:matrix.org @hackbunny:matrix.org | In reply to @joepie91:pixie.town
still not totally sure what magic trick Intel pulled to convince the skeptics in the case of Signal, it seems it was the promise of homomorphic encryption without homomorphic encryption | 00:58:03 |
 @hackbunny:matrix.org @hackbunny:matrix.org | In reply to @sarahjamielewis:matrix.org
There are a couple of levels worth considering for nuance:
SGX as implemented right now on most systems is fundamentally broken, many times over. There are several CPU bugs where patch rates are questionable and many others that are outright unpatchable (i.e. Load Value Injection). Last I checked Intels official response to this was "as long as you trust the OS to mitigate things properly it's not exploitable in the real world) which might be fine under some threat models, but is definitely not under ones we care about for something like Signal.
So anything that invokes SGX in its threat model is likely broken in practice, if not in theory. Invoking the "well I'm sure Signal patched their server OS" doesn't resolve the brokenness because it forces you to accept a trust assumption. (if you are willing to invoke that trust assumption then you don't need to bother with SGX at all - just trust signal to run the source code they say they run (which they sometimes don't publish for a year...but that's another thing entirely))
But, because the entire point of invoking a secure enclave is to protect your users from yourself then it's not just a case of auditing the source code, but also the entire operating system stack, continually - because the moment you take your eyes away from it it can be swapped out with something that makes it vulnerable.
In any case, as far as government agencies are concerned there is a spectrum from a targeted hack to an explicit backdoor. If a government could force Signals cooperation then there are likely far easier places to put a backdoor (like the client software, via a targeted poisoned appstore "upgrade"), so in terms of realistic exploits on the SGX side I'd be more concerned with a targeted hack (probably from states outside of jurisdictions where Signal operates).
* thank you! I admit my knowledge of SGX is extremely limited, so I wasn't aware that there would be so many ways to get it wrong
speaking of Signal specifically, the threat model I'm thinking of is a pure metadata compromise, where you can reconstruct who's talking with whom, without necessarily knowing what they're saying ("we kill people based on metadata"). besides timing analysis, to me the easiest way seems to be compromising the contact list server: it gives you a "god mode" view over the entire network, it's completely opaque to researchers, you can turn it on and off any time, and Whisper Systems can plausibly deny they knew anything about it. there's a certain degree of secrecy around the Signal servers dictated by anti-censorship considerations that helps here
personally, I'm not too worried about the rogue update attack: it leaves permanent evidence all over the place, it's much harder to plausibly deny, and it would destroy the reputation of Signal and Open Whisper Systems if it were discovered. easier to compromise the extremely opaque servers (lots of places to hide bad code in a server, too: think SMM, or SGX itself), identify the target through traditional techniques and/or metadata analysis and then phish them with a targeted attack, IMHO. wrt the client I think the most realistic attack is a vulnerability in a third party codec or the VoIP stack, especially on iOS where only iMessage has the privilege to put sensitive code in separate sandboxed processes
| 00:58:56 |
|  quadarcanum joined the room. quadarcanum joined the room. | 11:07:31 |
 sarahjamielewis
sarahjamielewis mconley
mconley
 joepie91 🏳️🌈
joepie91 🏳️🌈